Appearance
Host-based Firewall Management
Available in manifest version 19.0 and later.
Enclave offers the ability to manage the host-based firewall on deployed devices. This allows you to configure security groups from the EMC and have them applied to the host-based firewall on the device. This is useful for managing the firewall rules on your devices remotely and to lock down your network after migration to the Enclave overlay network.
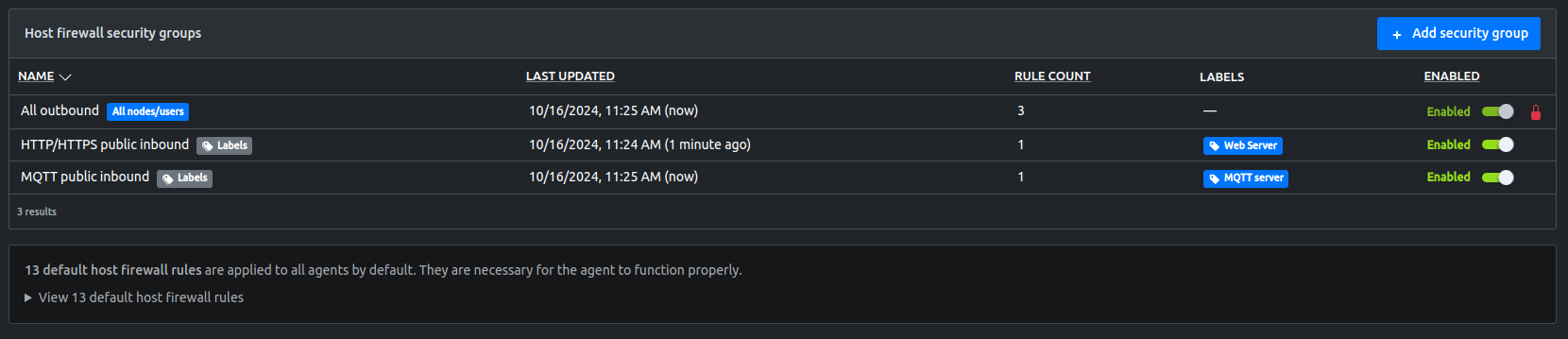 Security groups in the EMC
Security groups in the EMC
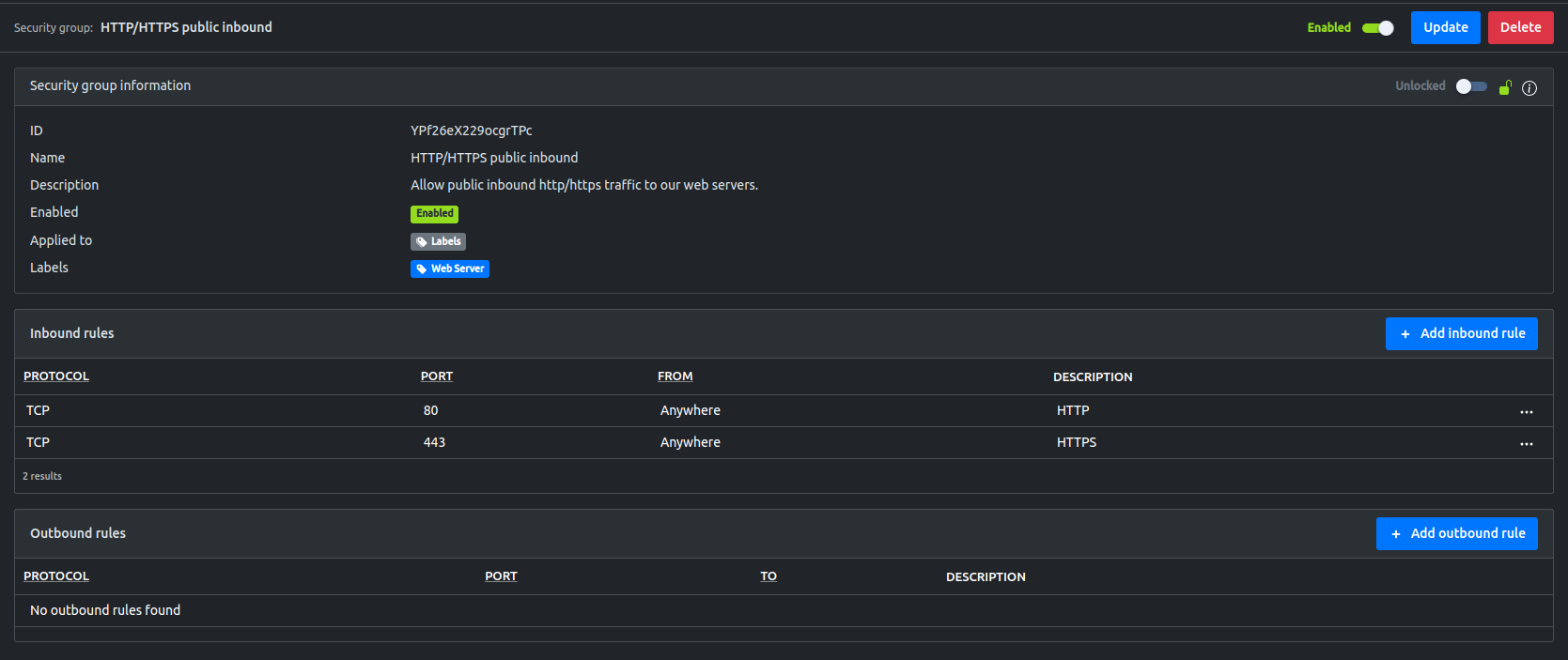 Managing a security group in the EMC
Managing a security group in the EMC
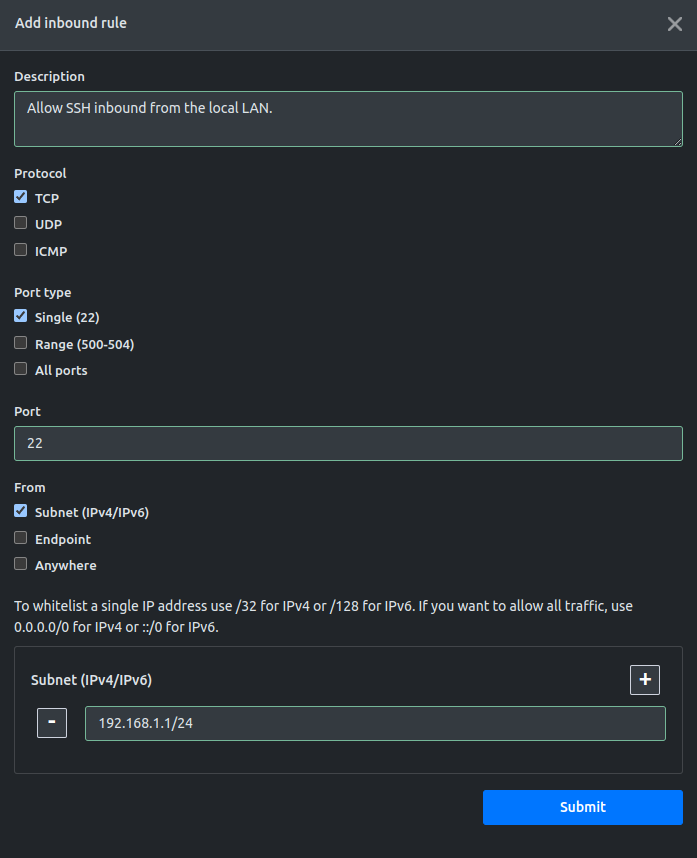 Adding a security group inbound rule
Adding a security group inbound rule
Supported platforms
The table below details the supported platforms for Enclave host-based firewall management.
| Windows | Linux | MacOS | |
|---|---|---|---|
| Supported | ✅ | ✅ | ✖️ |
| Implementation | Windows Filtering Platform (WFP) | nftables | ➖ |
| IPv4/IPv6 support | ✅ | ✅ | ➖ |
INFO
Host-based firewall is only available on node and user type agents. Beacon and virtual gateway agents do not support host-based firewall management. Physical gateways manage their bridge rules separately.
General notes
Enclave host-based firewall management is supported on Windows and Linux devices. MacOS devices are not supported at this time.
In order to manage the host-based firewall on a device, the device must have the Enclave agent installed and running. The agent is responsible for applying the security groups from the EMC to the host-based firewall on the device.
To ensure that the agent can still communicate with the EMC, default rules is applied in addition to the rules defined by the user. These default rules allows the agent to communicate with the EMC as well other necessary services (MQTT, beacons, agent update endpoints, VPN subnet). These default rules are visible in the EMC under the Firewall management view. DNS and DHCP traffic is also allowed by default to ensure that the device can still communicate with the network. If you have specific requirements for DNS and DHCP traffic (i.e. DoH), you will need to define the rules in the EMC before they are applied to the device or you risk losing connectivity.
By default, the EMC creates a disabled All outbound table. When adopting Enclave host-based firewall management, we recommend that you enable this table to ensure that all outbound traffic is allowed. For most devices this will ensure that connectivity is working as expected.
If the agent is logged out, the firewall state persists. If for any reason you need to reset the firewall completely, you can do so by logging out of the agent and running enclave firewall reset on the device. We maintain the state of the firewall, even when unauthenticated, to maintain compliance of the device.
Linux platform notes
Enclave uses nftables to manage the host-based firewall on Linux devices. This is a modern replacement for iptables and is the default packet filtering framework in the Linux kernel. nftables must be installed and active on the device for Enclave to manage the host-based firewall.
INFO
Note that our ruleset, similar to that of UFW, is on the inbound hook. If you are utilizing docker or any other services that do internal routing, you will need to manage those rules separately since traffic skips the inbound hook and goes directly to the forward hook. If this is a situation you are in, please reach out to us and we can help you manage these rules.
Installation steps
In most cases, nftables is already installed on a Linux device. To check if nftables is installed, you can run the following command:
bash
sudo nft --versionIf you need to install, an example of how to install nftables on a Debian-based distro is shown below:
bash
sudo apt install nftablesEnclave will then detect the nftables service and manage the host-based firewall on the device and be able to apply securty groups from the EMC.
Implementation details
Enclave creates a separate inet table for managing the host-based firewall on Linux devices. This table is named enclave and is used to apply rulesets from the EMC. The enclave table is created when the host-firewall has active rules returned from the EMC. If no rules are returned, the enclave table is not created.
Currently, host-firewall management can only be used for simple ingress and egress packet filtering. Actions such as dnat and bridge filtering must be done outside of the enclave table and managed externally.
When rules are updated, the agent will reapply the rules to the enclave table. This ensures that the ruleset from the EMC is applied correctly and bypasses any other rules that may be in place. When rules are updated, connections are re-evaulated to ensure that the new rules are applied correctly.
Our agent persists the state of the firewall even when unauthenticated. This is to ensure that the device remains compliant with the ruleset from the EMC. If the agent is logged out, the firewall state persists. If for any reason you need to reset the firewall completely, you can do so by logging out of the agent and running enclave firewall reset on the device.
Windows platform notes
Enclave uses the Windows Filtering Platform (WFP) to manage the host-based firewall on Windows devices. This is a set of API and system services that provide a platform for creating network filtering applications. The WFP is used by services such as Windows Defender Firewall and IPsec to implement network access control.
Implementation details
Enclave creates a WFP sublayer at the top of the filtering stack. This sublayer is used to apply permit or block verdicts based on the ruleset returned from the EMC. The WFP sublayer is created when the host-firewall has active rules returned from the EMC. If no rules are returned, the WFP sublayer will not exist.
When permit verdicts are applied at the enclave WFP sublayer, they are issued as a hard action so they can bypass lower rules in the filtering stack. This ensures that the ruleset from the EMC is applied correctly and bypasses any other rules that may be in place (i.e Windows Defender Firewall rules). Unless a veto is issued somewhere else on the WFP stack, the permit verdict will be applied.
The WFP sublayer rules are applied on the ALE connect layer. This is the layer that is responsible for the connection setup and teardown. This keeps packet processing to a minimum. When rules are updated, connections are re-evaulated to ensure that the new rules are applied correctly.
MacOS platform notes
Enclave does not support host-based firewall management on MacOS devices at this time. We are actively looking to add support for MacOS devices in the future.
Future improvements
- Add support for MacOS devices
- Collect dropped packets for analysis and alerting on the EMC

